Understanding Proofpoint URL Defense: Enhancing Cyber Security for Businesses
The Importance of Cyber Security in Today's Digital Landscape
In an era where businesses heavily rely on digital platforms, ensuring robust cyber security is paramount. The increasing prevalence of cyber threats such as phishing, ransomware, and other malicious attacks has made it crucial for organizations to adopt comprehensive security measures. One such innovative solution is the Proofpoint URL Defense, which plays a vital role in protecting sensitive information and preserving the integrity of business operations.
What is Proofpoint URL Defense?
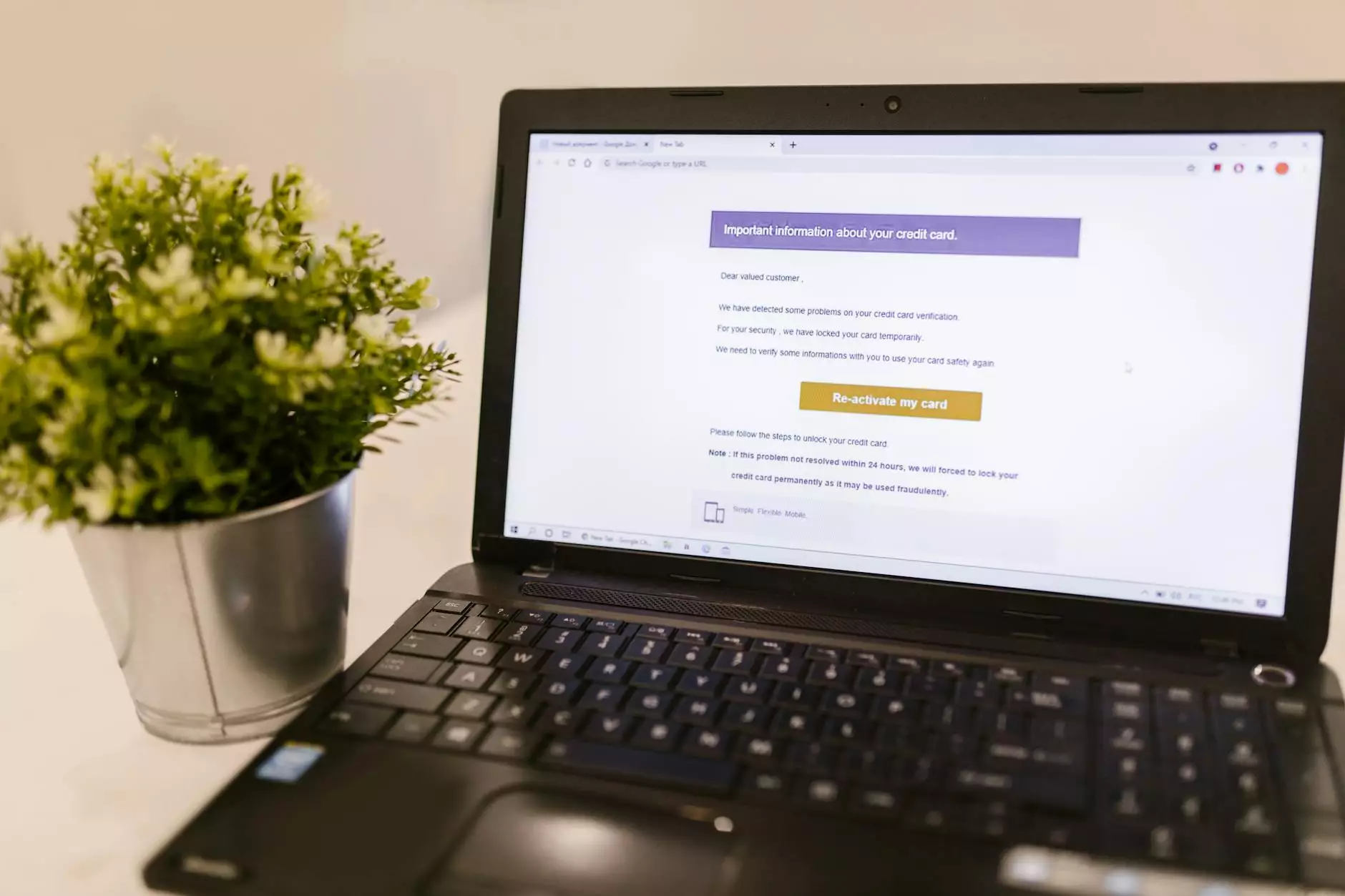
Proofpoint URL Defense is a security service that provides advanced protection against phishing attacks and other URL-based threats. It functions by analyzing URLs in incoming emails and other communications, and it effectively mitigates there risks posed by malicious links. The solution is particularly beneficial for businesses in sectors such as IT Services and Computer Repair, where safeguarding client data is critical.
Key Features of Proofpoint URL Defense
Understanding the features of Proofpoint URL Defense is essential for any business seeking to fortify its security posture. Here are some of the highlighted features:
- Real-Time URL Scanning: Every URL linked in emails is scanned in real-time to identify potential threats before they can be accessed by users.
- Reputation Scoring: Proofpoint evaluates the reputation of the URL based on its history, helping users make informed decisions before clicking.
- Link Rewriting: The service rewrites hyperlinks to redirect through Proofpoint's security checks, ensuring that users only access safe destinations.
- Threat Intelligence Integration: The system leverages vast databases of known threats, continuously updated to protect organizations against emerging vulnerabilities.
- Detailed Reporting and Analytics: Businesses receive insights into attempted threats, helping them refine their security strategies accordingly.
Benefits of Implementing Proofpoint URL Defense
Businesses that implement Proofpoint URL Defense reap numerous benefits:
1. Enhanced Protection Against Phishing
Phishing attacks are among the most common cyber threats. By deploying Proofpoint URL Defense, businesses dramatically reduce the likelihood of falling victim to these schemes. The effective scanning and real-time analysis minimize exposure to harmful links.
2. Safeguarding Brand Reputation
For companies in IT Services and Computer Repair, maintaining a good brand reputation is crucial. A single security breach can lead to a loss of trust among clients. By utilizing Proofpoint’s solution, organizations can ensure they protect their customers, thereby reinforcing their brand image.
3. Boosting Employee Security Awareness
Integrating Proofpoint URL Defense into everyday operations offers an additional layer of security, but it also serves as an educational tool. Staff become more aware of potential threats, leading to a more security-conscious workplace.
4. Reduced IT Costs
Many businesses find themselves incurring significant costs associated with data breaches and remedial actions. By proactively using solutions like Proofpoint, organizations can mitigate these costs, effectively reducing the total spend on IT security-related issues over time.
How Does Proofpoint URL Defense Work?
Understanding the operational workflow of Proofpoint URL Defense provides greater insight into its effectiveness:
- URL Linking: When a user receives an email containing a link, the URL is rewired to route through Proofpoint’s security system.
- Analysis: The URL undergoes real-time analysis using various algorithms and databases to assess its safety.
- access Check: If the URL is deemed safe, the user is directed to the original link; if not, a warning page is presented.
- Reporting: All actions are logged and reported to the system administrator, providing transparency and insights into potential threats.
Integrating Proofpoint URL Defense into Business Operations
Integrating Proofpoint URL Defense into existing IT services is a straightforward process. Here are several steps organizations can take to ensure a smooth integration:
1. Assess Current Security Posture
Before implementing any new system, it’s essential to evaluate the current security measures in place. Conducting a thorough risk assessment will help identify weaknesses and the necessity for a solution like Proofpoint.
2. Engage IT Professionals
Collaborating with IT experts is crucial to effectively implement and manage the Proofpoint URL Defense solution, ensuring it aligns with existing network protocols.
3. Provide Training for Employees
To maximize the benefits of Proofpoint, ensure that all employees receive training on how to recognize phishing attempts and understand the role of the new security measures.
4. Monitor and Adjust
After implementation, organizations should regularly monitor the effectiveness of the system, making necessary adjustments based on employee feedback and threat data.
Case Studies: Success Stories with Proofpoint URL Defense
Numerous organizations have successfully implemented Proofpoint URL Defense and have reported significant improvements in their cybersecurity posture. Here are a couple of examples:
Case Study 1: A Mid-Sized IT Firm
A mid-sized IT services company implemented Proofpoint to address growing security concerns. After deployment, the firm noticed a decrease in phishing attempts by over 70%, and there were no reported breaches in customer data over the subsequent year.
Case Study 2: A Computer Repair Business
A local computer repair business found itself targeted by multiple phishing schemes. By adopting Proofpoint URL Defense, the business was able to thwart several attempts, thus safeguarding its customer information and enhancing client trust.
Conclusion
As businesses continue to navigate the complexities of the digital realm, solutions like Proofpoint URL Defense play an indispensable role in securing sensitive data and maintaining trust in business relationships. For companies in IT Services and Computer Repair, this proactive approach to cyber security is not just a safeguard; it is a strategic advantage in the competitive landscape.
By integrating such advanced security measures, organizations can focus on growth, innovation, and providing exceptional service to their clients, free from the looming threat of cyber attacks. Choosing Proofpoint URL Defense signifies a commitment to providing not only a secure environment for operations but also peace of mind for businesses and their customers alike.









